This post is the second out of three blog posts summarizing my (Louis Jannett) research on the design, security, and privacy of real-world Single Sign-On (SSO) implementations. It is based on my master's thesis that I wrote between April and October 2020 at the Chair for Network and Data Security.
We structured this blog post series into three parts according to the research questions of my master's thesis: Single Sign-On Protocols in the Wild, PostMessage Security in Single Sign-On, and Privacy in Single Sign-On Protocols.
Overview
Although previous work uncovered various security flaws in SSO, it did not work out uniform protocol descriptions of real-world SSO implementations. We summarize our in-depth analyses of Apple, Google, and Facebook SSO. We also refer to the sections of the
thesis that provide more detailed insights into the protocol flows and messages.
It turned out that the postMessage API is commonly used in real-world SSO implementations. We introduce the reasons for this and propose security best practices on how to implement postMessage in SSO. Further, we present vulnerabilities on top-visited websites that caused DOM-based XSS and account takeovers due to insecure use of postMessage in SSO.
Identity Providers (IdPs) use "zero-click" authentication flows to automatically sign in the user on the Service Provider (SP) once it is logged in on the IdP and has consented. We show that these flows can harm user privacy and enable new targeted deanonymization attacks of the user's identity.
Introduction to XS-Leaks in Single Sign-On
Cross-site leak (XS-Leak) refers to a family of browser side-channel techniques that can be used to infer and gather information about users [...]. While the deanonymization capabilities of XS-Leak attacks are only just being realized, some researchers have said the technique will soon be in the OWASP Top 10.
In SSO setups, redirects can leak private information about the user. Thus, we focused on XS-Leaks that detect cross-origin redirects, i.e., whether a cross-origin request returns an `HTTP/200` or `HTTP/302` response. In this post, we present an XS-Leak that is based on the Fetch API and detects cross-origin redirects with 100% accuracy. The following method expects a URL, sends a GET request, and finally returns `true` if the response is a redirect or `false` if the response is no redirect:
// let is_redirect = await xs_leak_redirect("<URL>"); async function xs_leak_redirect(url) { let res = await fetch(url, { mode: "cors", credentials: "include", redirect: "manual" }).then( (response) => { if (response.type == "opaqueredirect") { return true; } }).catch( (error) => { return false; }); return res; }
XS-Leaks in Single Sign-On: Account Leakage Attack
With the account leakage attack, the attacker can determine whether the victim has an account on a targeted SP with a certain IdP. Specifically, the attacker checks whether the victim has granted consent to the targeted SP with the IdP. This attack is scalable: The attacker can test multiple (SP, IdP) pairs and check for which pair the victim has an account on the SP. The following prerequisites must hold:
- The victim visits an attacker-controlled website.
- The victim is signed-in on the IdP (i.e., in Google Chrome with its Google account).
- The IdP supports the standardized `prompt=none` parameter.
The attack idea is simple: Let's assume the attacker wants to know whether the victim has an account on SP `
sp.com` with the IdP `
idp.com`. The attacker first tricks the victim into visiting its malicious website `
attacker.com`. We further assume that the victim has an active session on the IdP. Then, the attacker constructs an Authentication Request URL, as shown in the figure below. Note that the SP `
sp.com` has the `
client_id=superSecretClient` on the IdP, the `
redirect_uri` is set to `
sp.com/redirect`, and the `
prompt=none` parameter is set.
From the attacker's website, a cross-origin `Fetch` request is sent to that URL as shown
before. If the `
prompt=none` flow is requested with established consent on the SP, the IdP returns the Authentication Response as an `
HTTP/302` redirect to the `
redirect_uri`. If the victim has not granted the SP's consent, the IdP returns the consent page with an `
HTTP/200` response and asks the user to grant the consent. Thus, based on whether the victim has or has not an account on `
sp.com`, the IdP returns an `
HTTP/302` redirect or an `
HTTP/200` response. Although the Same Origin Policy prevents us from viewing the response from `
idp.com`, we can use the XS-Leak to detect whether a redirect was performed or not. If a redirect was performed, the victim has an account on `
sp.com` with the IdP. If no redirect was performed, the victim has no account.

We tested this attack with the Apple, Google, and Facebook IdP. It only works for Google and Facebook since Apple requires user interaction in each flow. A working PoC is provided on
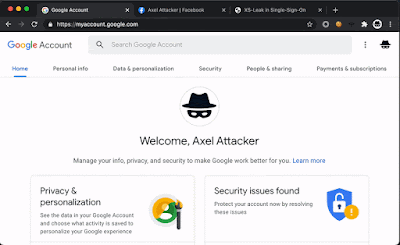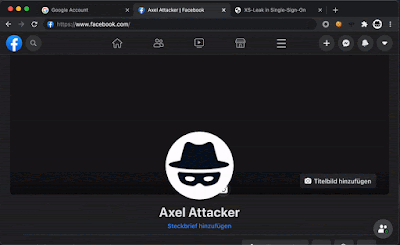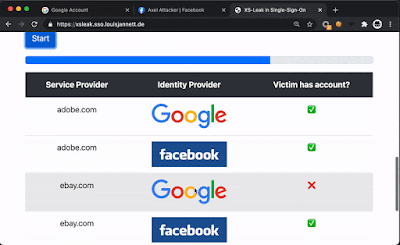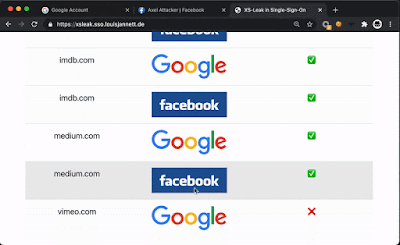
https://xsleak.sso.louisjannett.de. If the "Start" button is clicked, the website checks if you have an account on
adobe.com,
ebay.com,
imdb.com,
medium.com, or
vimeo.com using either the Google or Facebook IdP. Make sure that you are signed in at Google and Facebook before testing and enable third-party cookies.
To circumvent this attack, the IdP must return an error as `
HTTP/302` redirect if the `
prompt=none` flow is requested, but no consent is given. This mitigation is described in the
OpenID Connect specification, but as shown, not adopted by real-world IdPs.
XS-Leaks in Single Sign-On: Identity Leakage Attack
The identity leakage attack extends the account leakage attack by the `login_hint` parameter. The attacker can determine whether the victim has a certain identity on a targeted IdP. The attacker can use this information to check if a certain person is visiting its website. Therefore, all prerequisites of the account leakage attack must hold and the IdP must support the standardized `login_hint` parameter.
Once a victim visits the malicious website, the attacker must initially guess an (SP, IdP) pair that the victim most likely gave consent to, i.e., that causes the IdP in the `prompt=none` flow to return a redirect to `sp.com/redirect`. The attacker can use the account leakage attack to determine such a pair by testing the most-popular SPs and IdPs. Then, a new Authentication Request is created, and the `login_hint` parameter is set to the email address of the victim, i.e., `alice@example.com`. The attacker sends the Fetch request and determines whether the IdP returns an `HTTP/302` redirect or an `HTTP/200` response. If a redirect was performed, the attacker knows that the Authentication Request was valid, and thus the victim is `alice@example.com`. If no redirect was performed, the victim is not `alice@example.com`. The success of this attack depends on whether the attacker can guess (or eventually knows) an (SP, IdP) pair that the targeted victim gave consent to.

We tested this attack with the Apple, Google, and Facebook IdP. It only works for Google since Apple does not support the `prompt=none` flow, and Facebook does not support the `login_hint` parameter. We discovered that the `login_hint` parameter must contain a valid email address registered at Google. Otherwise, this parameter is ignored.
To mitigate this leakage, the IdP must return an error as `
HTTP/302` redirect if a `
login_hint` parameter is queried that the user does not own. We did not find any information about the `
login_hint` parameter in the
OpenID Connect specification that proposes guidelines for this scenario.
Automatic Sign-In and Session Management Practices in the Wild
Following the observations of the account leakage and identity leakage attacks, we analyzed "zero-click" SSO flows in terms of automatic sign-in features provided by the IdPs with their SDKs. We found that under certain assumptions, the SDKs can be configured to automatically sign in the user on the SP even though the user did not click on the sign-in button and may not notice the sign-in process.
Google and Facebook support automatic sign-in with their SSO SDKs: Google Sign-In, Google One Tap, and Facebook Login. They follow a similar approach: The user visits the SP website that integrates and initializes the SDK with automatic sign-in enabled. Suppose the user has an active session on the IdP, valid consent for the SP, and third-party cookies enabled. In that case, the SDK first retrieves a logout state from browser storage to determine whether the user signed out previously using the SDK's sign-out method. If the logout state is set to false or does not exist, the SDK returns the Authentication Response to the SP website, i.e., to a registered callback. If it is set to true, the SDK does not proceed with the automatic sign-in and instead requires the user to click on the sign-in button. Thus, the execution of the automatic sign-in flow depends on the stored logout state. If the browser storage is cleared (i.e., cookies are deleted or a private window is opened), the logout state does not exist, and thus the automatic sign-in is enabled.
Note that the logout state is only a feature provided by the SDKs to stop unwanted sign-in operations on the SP. They do not prevent the SP from secretly receiving tokens from the IdP. If the SP does not use the SDK's sign-out method, the logout state will never be set to true. Alternatively, the SP may manually request the tokens from the IdP in the background without paying attention to any logout state. Note that this automatic sign-in flow is different than the standardized `prompt=none` flow because it returns the tokens in the background (i.e., via Fetch requests), whereas the `prompt=none` flow requires a redirect that is in some form visible to the user.
Google and Facebook use different approaches to receive the Authentication Response in the background. Google sends a `getTokenResponse` RPC from the SP website to its proxy iframe and receives the tokens with postMessage. Facebook issues a simple CORS request and receives the tokens in the CORS response.
For instance, SPs can send the following CORS request with the Fetch API to Facebook:
GET /x/oauth/status?client_id=<CLIENT_ID> HTTP/1.1 Host: www.facebook.com Origin: https://sp.com Cookie: c_user=REDACTED; xs=REDACTED;
If the user has an active session at Facebook (i.e., cookies are set) and valid consent, Facebook responds with a CORS response and explicitly allows the SP to read the `fb-ar` header that contains the tokens:
HTTP/1.1 200 OK Access-Control-Allow-Origin: https://sp.com Access-Control-Allow-Credentials: true Access-Control-Expose-Headers: fb-ar,fb-s fb-s: connected fb-ar: {"user_id": "REDACTED", "access_token": "REDACTED", "signed_request": "REDACTED"}
We tested the automatic sign-in on top-visited SPs and found that some of them implement it as expected. For instance, `change.org` supports automatic sign-in with Facebook: First, we open `change.org` without being logged in on Facebook. Thus, we are not signed-in automatically. Then, we log in on Facebook and reload `change.org`. As shown, `change.org` uses the CORS request to receive the tokens from Facebook and finally logs us in. The user interface does not indicate that we were just signed in. Only the small profile picture in the top right corner is added to the UI.
Acknowledgments
Also, special thanks to
Lauritz for his feedback on this post and valuable discussions during the research. Check out his blog post series on
Real-life OIDC Security as well.
Authors of this Post
Louis Jannett
- Hack Tools For Ubuntu
- Hacker Tools Mac
- Hacking Apps
- How To Install Pentest Tools In Ubuntu
- Kik Hack Tools
- Hacker Tools Apk Download
- Kik Hack Tools
- Hacker Tools Free
- Hack Website Online Tool
- Install Pentest Tools Ubuntu
- Hackers Toolbox
- Hack Rom Tools
- Android Hack Tools Github
- New Hacker Tools
- Tools For Hacker
- Wifi Hacker Tools For Windows
- Hack Tools Download
- Hacker Hardware Tools
- Tools Used For Hacking
- Hacker Tools Free Download
- Hack Tools For Mac
- Hacker Tools Mac
- Hack Tools
- Hacking Tools For Windows 7
- What Are Hacking Tools
- Install Pentest Tools Ubuntu
- Pentest Tools Review
- Beginner Hacker Tools
- Hak5 Tools
- Hack And Tools
- Hacking Tools 2020
- Hacks And Tools
- Hacking Tools For Windows
- Nsa Hack Tools
- Termux Hacking Tools 2019
- Hacker Tools For Ios
- Hack Tools For Games
- Hacking Tools For Kali Linux
- Hacker Tools
- Hack Tools
- Pentest Tools Open Source
- Pentest Tools For Ubuntu
- Beginner Hacker Tools
- Hacking Tools And Software
- Hacker Tools Online
- Ethical Hacker Tools
- Hacker Tool Kit
- Hack Tools Download
- How To Hack
- Hacking Tools Mac
- Hacker Tools 2020
- Blackhat Hacker Tools
- Install Pentest Tools Ubuntu
- Hack Tool Apk No Root
- Kik Hack Tools
- Hacking Tools Name
- Hacker Techniques Tools And Incident Handling
- Hacker Hardware Tools
- What Are Hacking Tools
- Hacking Tools Hardware
- Pentest Tools
- Easy Hack Tools
- Hack Website Online Tool
- Pentest Tools Url Fuzzer
- Hacker Tools For Pc
- Hack Tools
- Usb Pentest Tools
- Android Hack Tools Github
- Pentest Tools Linux
- Hack Tools Github
- Pentest Tools Android
- Hacking Tools 2020
- Hacks And Tools
- Kik Hack Tools
- Hacking Tools 2019
- Pentest Tools Alternative
- Hacking Tools Windows
- Pentest Tools Nmap
- Hacker Tools
- How To Hack
- How To Make Hacking Tools
- Hacking Tools For Beginners
- Hacking Tools For Kali Linux
- Hack Tools Online
- Hack Tools For Windows
- Pentest Tools List
- Pentest Tools For Windows
- Hacking Tools For Mac
- Hacker Tools Online
- Hacker Tools
- Pentest Tools Tcp Port Scanner
- Hack Tools For Ubuntu
- Hacker Tools Github
- Pentest Tools Url Fuzzer
- Github Hacking Tools
- Beginner Hacker Tools
- Hacker Tools Windows
- Hack Website Online Tool
- Underground Hacker Sites
- Hacking Tools Free Download
- Pentest Tools Website Vulnerability
- Nsa Hack Tools Download
- Hacking Tools Mac
- Hacker Techniques Tools And Incident Handling
- Hacker Tools Windows
- Hacking Tools Kit
- What Is Hacking Tools
- Free Pentest Tools For Windows
- Pentest Tools Windows
- Pentest Tools Website
- Hack Website Online Tool
- Pentest Tools Port Scanner
- Hacker Tools Mac
- Hacking Tools For Mac
- Hacker Tools Apk Download
- Hacking Tools
- Hack Tool Apk No Root
- Pentest Tools Open Source
- Pentest Tools Apk
- Best Pentesting Tools 2018
- Hack Tools For Ubuntu
- Best Hacking Tools 2020
- Hack App
- Hack Tools Mac
- Pentest Automation Tools
- Hacking Tools Kit
- New Hack Tools
- Pentest Tools Website Vulnerability
- Hackers Toolbox
- Hacking Tools Github
- Hacker Techniques Tools And Incident Handling
- Pentest Tools For Ubuntu
- Hack And Tools
- Pentest Tools Github
- Hack Apps
- Hacker Tools List
- Pentest Tools Find Subdomains
- Best Hacking Tools 2019
- Hacker Tools For Mac
- Hacker Security Tools
- Best Hacking Tools 2019
- Hacker Tools For Ios
- Hacking Tools Mac
- Hacking Tools Windows 10
- Pentest Tools Download
- Pentest Reporting Tools
- Pentest Tools For Android
- World No 1 Hacker Software
- Pentest Reporting Tools
- Hacker Tools For Mac